LANeye Small Network Edition is a network monitoring software tool which main functionality is to detect illegitimate attempts to access your Local Area Network (LAN), and block those intruders. This program counts on specific features to improve security of your wireless environments, which are especially susceptible to be illegally accessed and/or hacked.
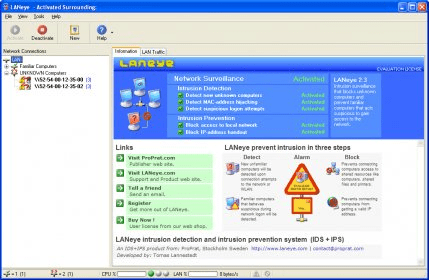
When you install LANeye, it acts as a system service, monitoring all the network traffic and always ready to stop any unwanted access. Its well-designed interface offers a single window with several panels that contain all the necessary information. On the one hand, you have the "LAN Traffic" tab, where all the network traffic detected by LANeye is shown. Here you can see very detailed information, such as the timestamp, the source and destination MAC addresses the package length, the protocol, the source and destination IP addresses and ports, and the IP type. On the other hand, you have also the "Information" tab, where you can activate or deactivate the different sub-services this program provides. Here you can establish if the program must detect new unknown computers, MAC address hijacking, suspicious logon attempts, block access to local network, and block IP address handout.
The main window also provides you with access to reports for both the “familiar” and the “unknown” computers. Furthermore, you can see the event's details for every blocked access attempt. It is very important to note that you must specify a particular network adapter in order to be able to activate the service, and thus get access to the reports mentioned above. On this window, you can also see the CPU usage and the LAN traffic speed as percentages, and the number of accepted and refused network connections. In addition, it shows shortcuts for activating or deactivating the service and creating new network monitoring profiles. When you close the program, it asks you if you want to completely close it, or just minimize it and keep the service running (in which case you can see it as an icon on the system tray area), which may help you to avoid cancelling the protection it provides accidentally.
Apart from all that, the program allows you to configure its detection and blocking sensitivity, make a detailed configuration of the local network access and IP handout blocking, and set the alarms (when they should be active and how they should behave). To sum up, I must say this is a great network monitoring tool that provides you with total control over who is trying to connect to your computer or local network.
Comments